Kafka is only as secure as its weakest link
While you're securing the front door with mutual TLS and SASL, self-managed Kafka leaves windows open through incomplete access controls, unmanaged secrets, and missing audit trails. Enterprise streaming in Europe demands security designed into every layer, not retrofitted when regulators arrive.
.svg)




.avif)




.svg)




.avif)




.svg)




.avif)





The Kafka security gaps your auditor will find
Your Kafka works perfectly until someone asks: 'Who changed that schema?', 'Which apps accessed patient data last month?' or 'Show us your key rotation logs.' That's when theory meets regulatory reality.
.svg)
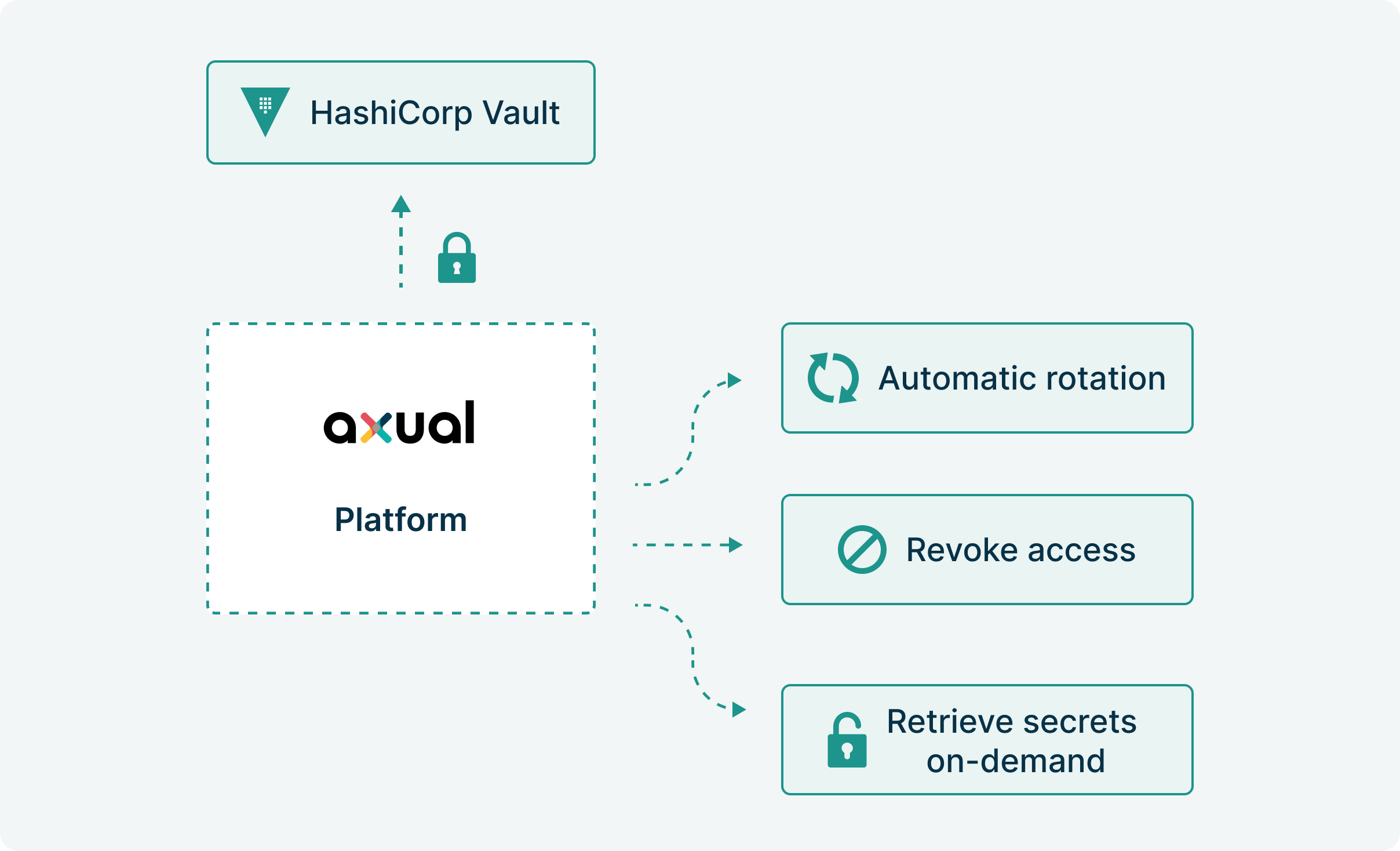
Credential sprawl chaos
Every producer needs credentials. Every consumer too. Soon you're managing hundreds of certificates across your infrastructure. Whose key is this? Where is it used? One leaked key compromises everything downstream.
.svg)
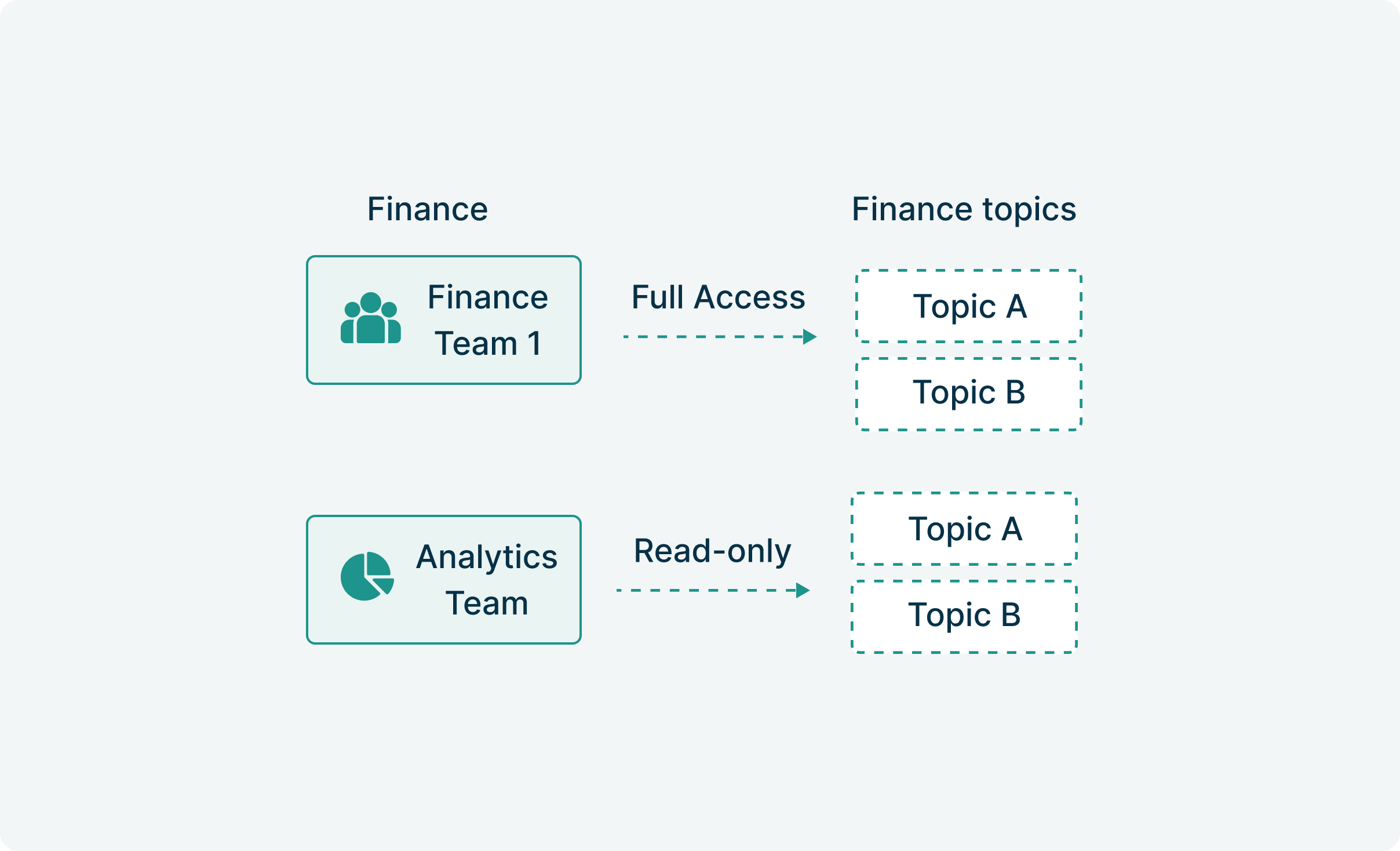
Multi-tenant isolation failures
Kafka ACLs weren't designed for enterprise multi-tenancy. When Team A accidentally reads Team B's payment data, explaining "misconfiguration" won't satisfy regulators.
.svg)
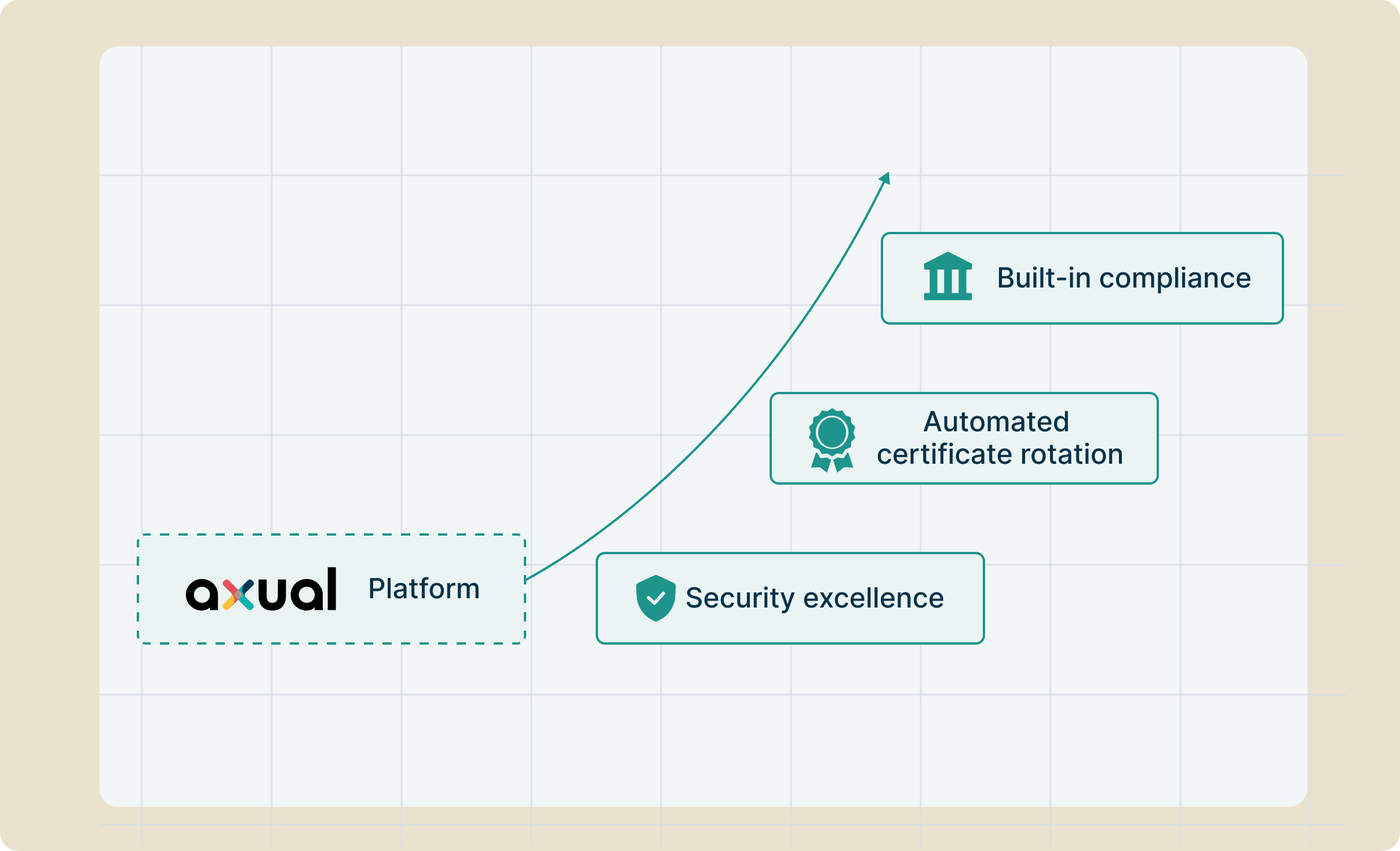
Compliance audit nightmares
Auditors want proof: Who accessed what data? When? Why? Your self-managed Kafka's authentication logs aren't audit trails. GDPR fines don't care about good intentions.
.svg)
End-to-end encryption complexity
TLS between brokers? Check. Client encryption? Check. Schema Registry security? REST Proxy authentication? Connector credentials? Your compliance checklist never ends.
.svg)
Schema evolution risks
Anyone can evolve schemas in standard registries. One wrong field deletion corrupts downstream systems. Schema governance isn't optional: production demands it.
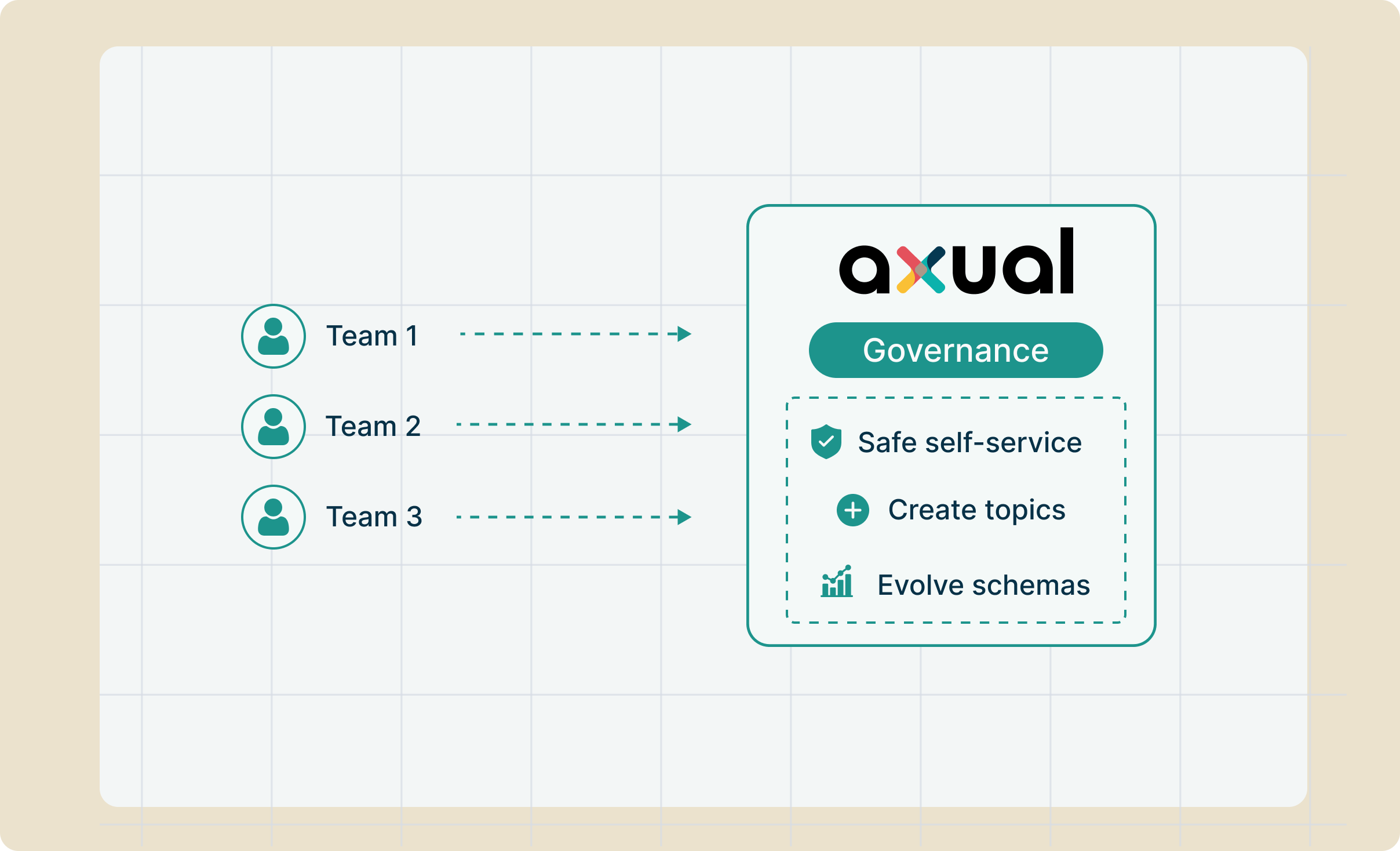
Governance at every layer
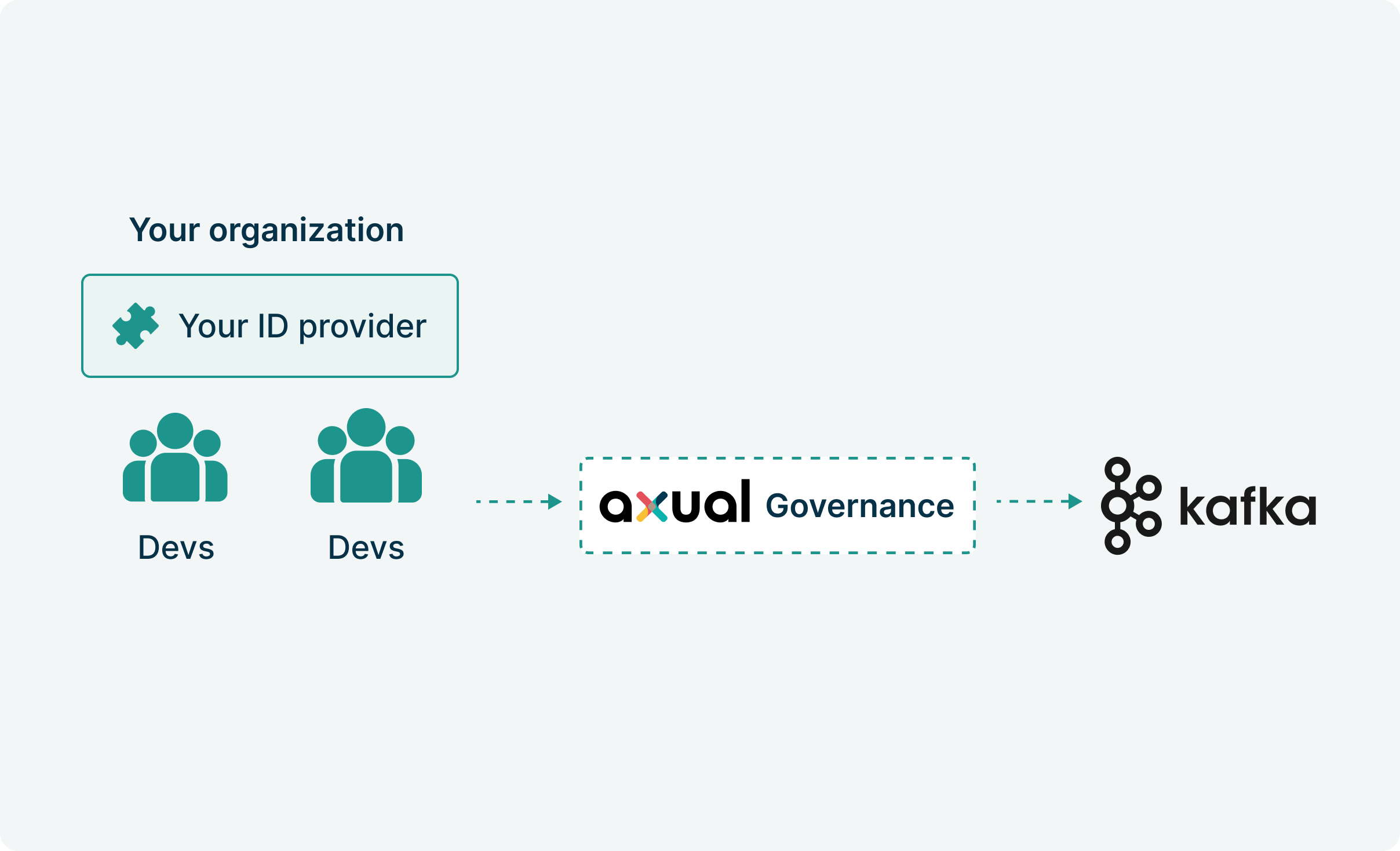
Axual embeds security into every layer of your streaming platform. Identity management, network isolation, and audit trails.
Built in from day one for mission-critical European infrastructure.
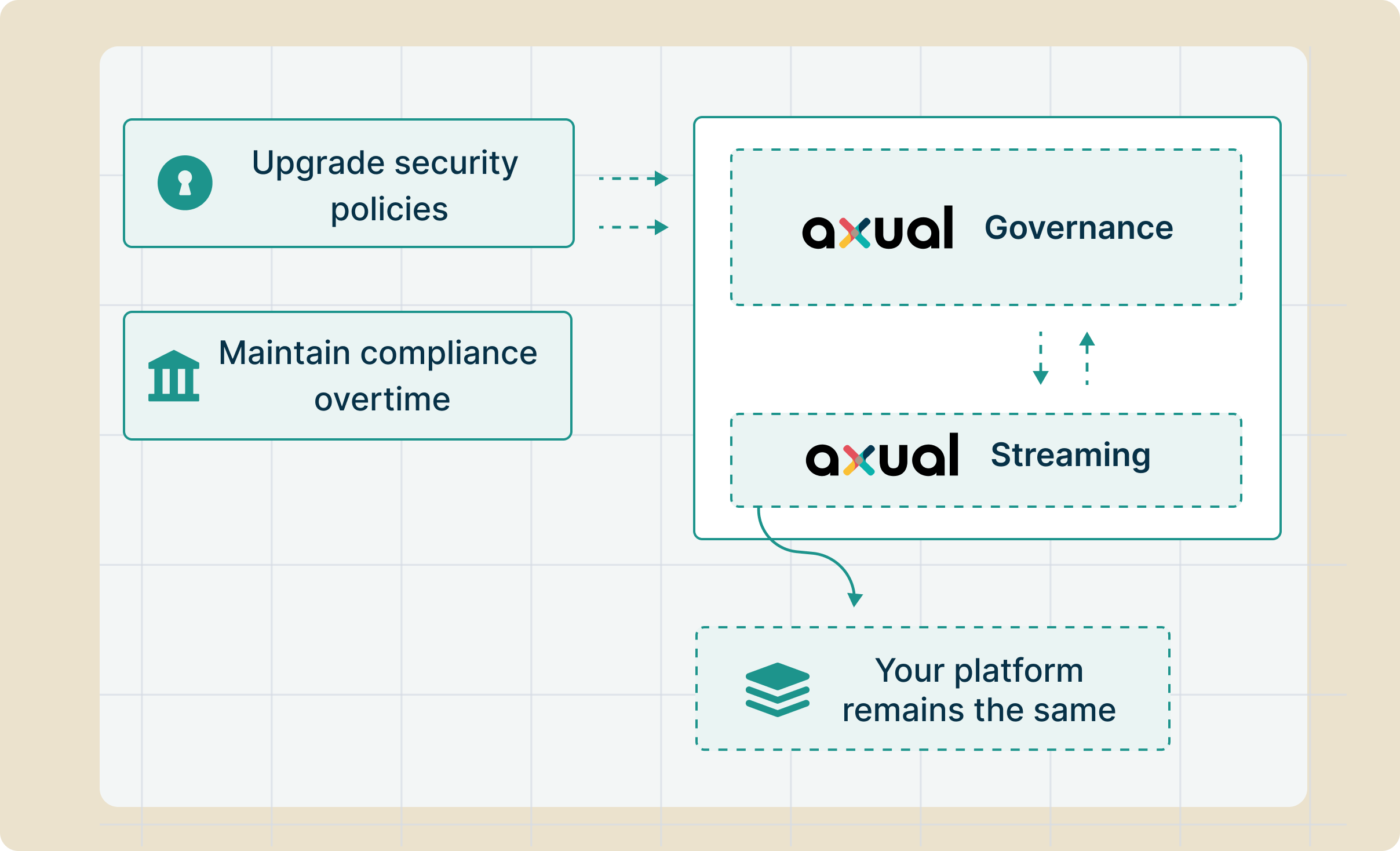
Proven in production, built for tomorrow
Security requirements intensify yearly. New regulations emerge, threats evolve, auditors demand more. Yesterday's compliance becomes tomorrow's violation. Build on architecture that adapts, not patches that accumulate.
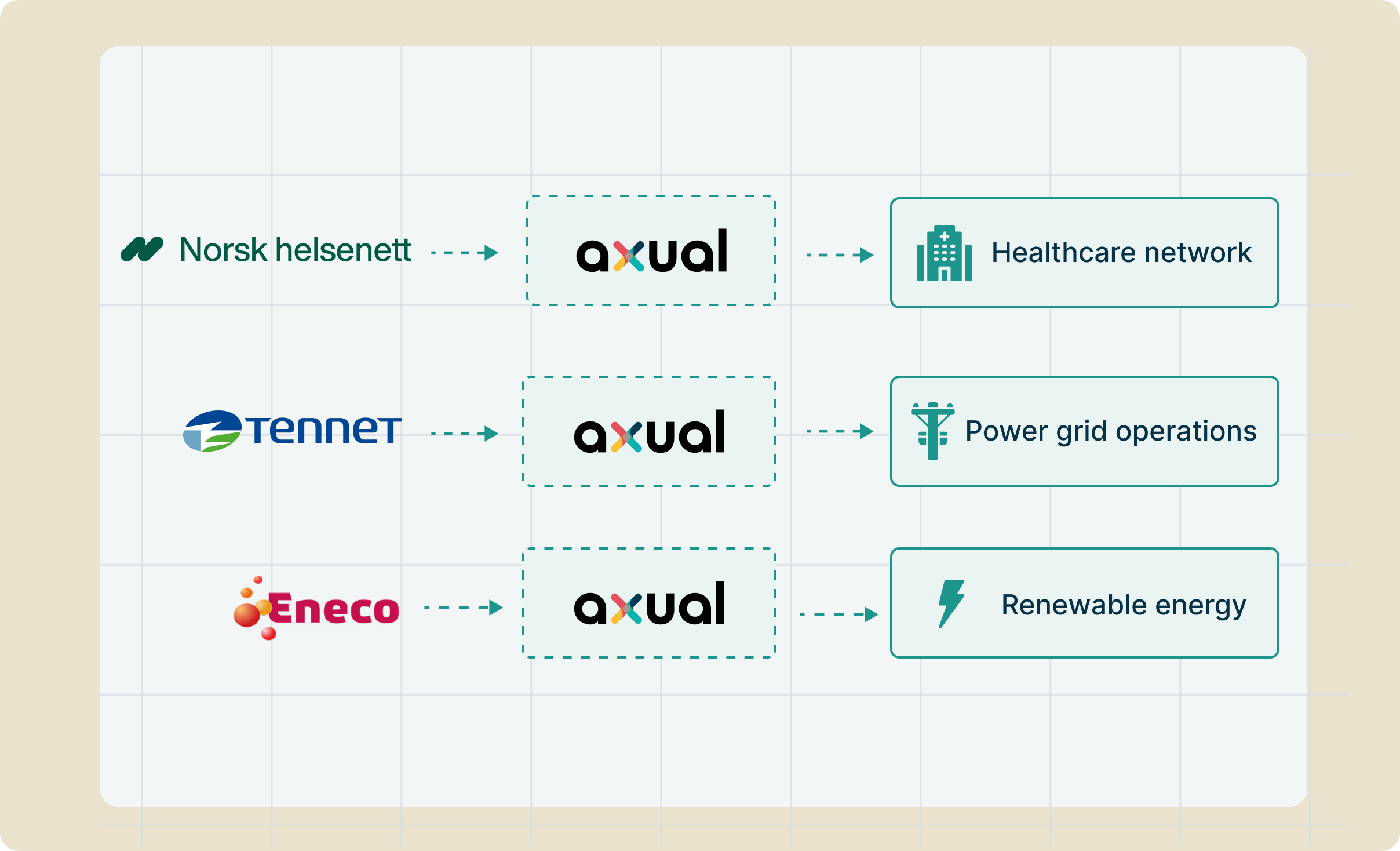
Use cases
Empower your team to unlock insights and drive decisions with our intuitive Kafka platform.

.svg)
.svg)
.svg)
.svg)