Axual Governance:
Control built in
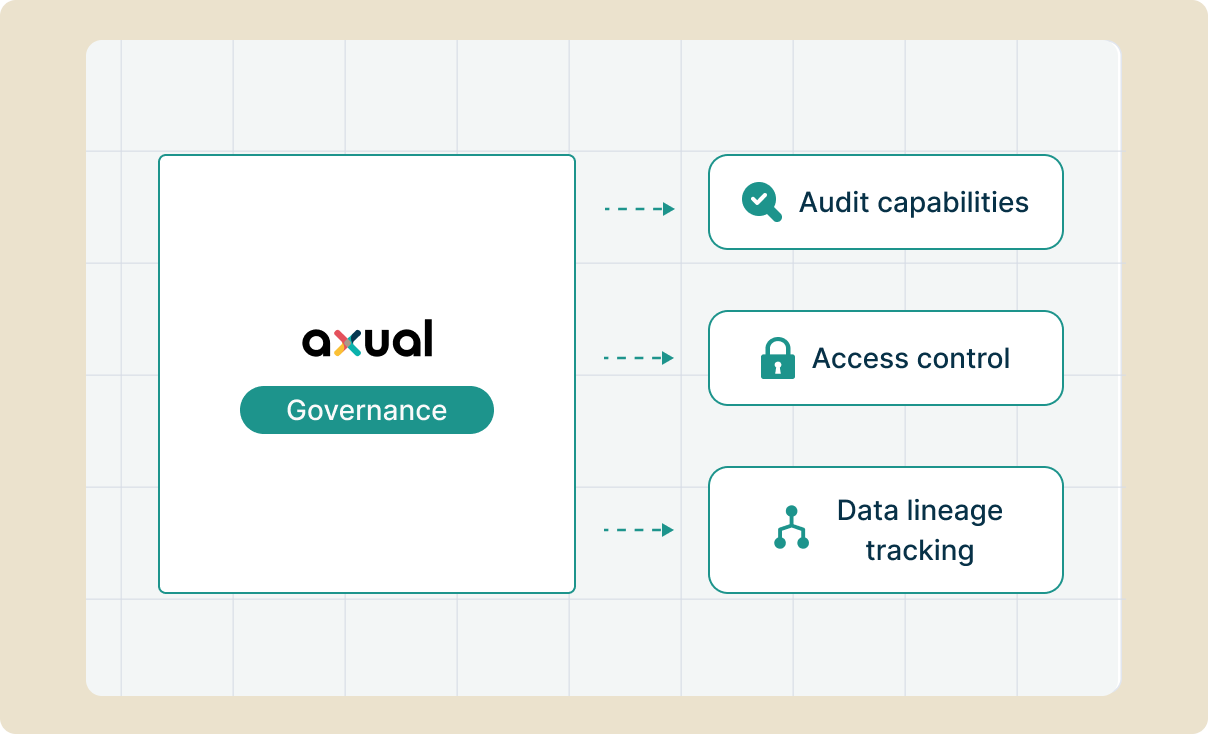
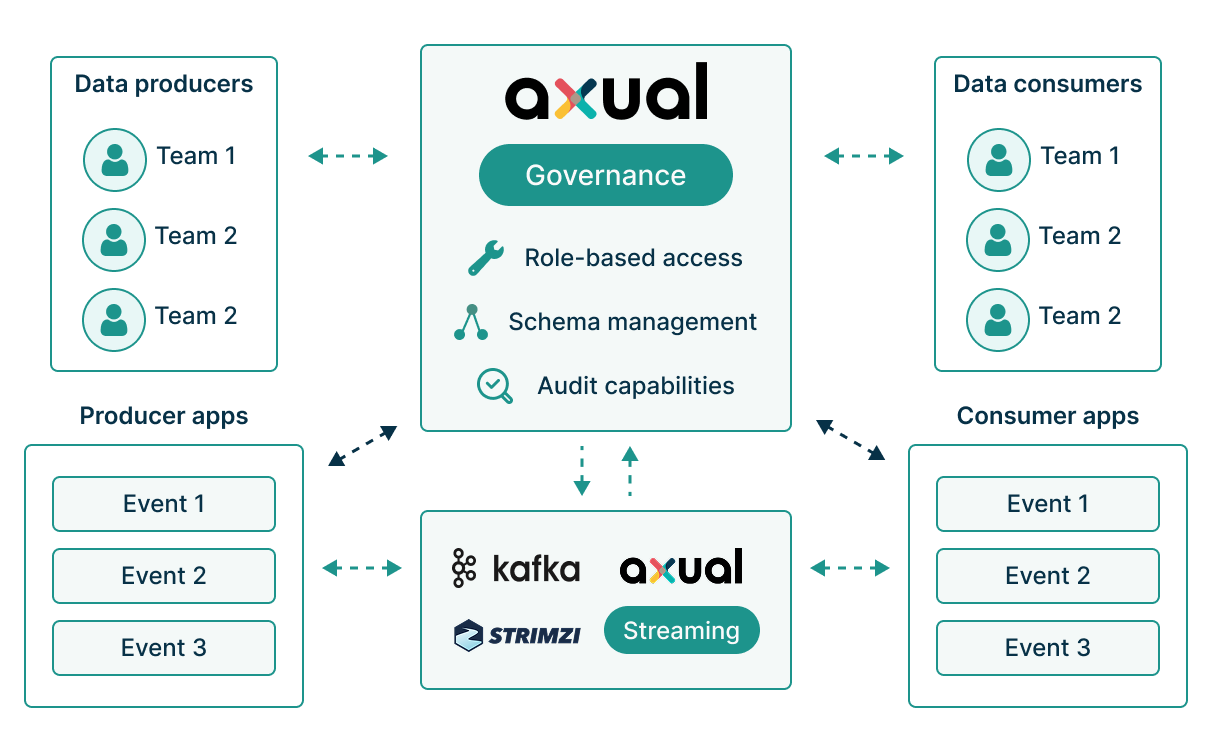
Axual Governance provides centralized control over your streaming infrastructure. Role-based access control, audit capabilities, and schema management work together to ensure your architecture remains compliant as regulatory requirements evolve.
.svg)




.avif)




.svg)




.avif)




.svg)




.avif)





How Governance works
Core Governance capabilities
Effective Kafka governance requires more than access control. Schema evolution, audit trails, and multi-environment consistency are equally critical. Axual delivers these capabilities through integrated components that work together seamlessly.
.svg)
Role-based access control
Define who can provision topics, deploy applications, or modify configurations. Map permissions to your organizational structure through groups and roles.

Schema registry
Control schema evolution across your streaming ecosystem. Enforce compatibility rules and track all versions with full lineage.

Audit Trail
Track every governance action with immutable logs. Meet compliance requirements for data lineage and access history.

API-First Architecture
Automate governance through REST APIs or Terraform. Integrate with CI/CD pipelines and GitOps workflows.

Connector management
Deploy Kafka Connect connectors through governance controls. Configure database, messaging, and cloud integrations with full audit trails.

Streaming applications
Run KSML applications with built-in governance. Deploy stream processing logic without compromising security policies.

G2 Easiest To Do Business With
.png)
G2 High Performer
Answers to your questions about Axual’s All-in-one Kafka Platform
Are you curious about our All-in-one Kafka platform? Dive into our FAQs for all the details you need, and find the answers to your burning questions.
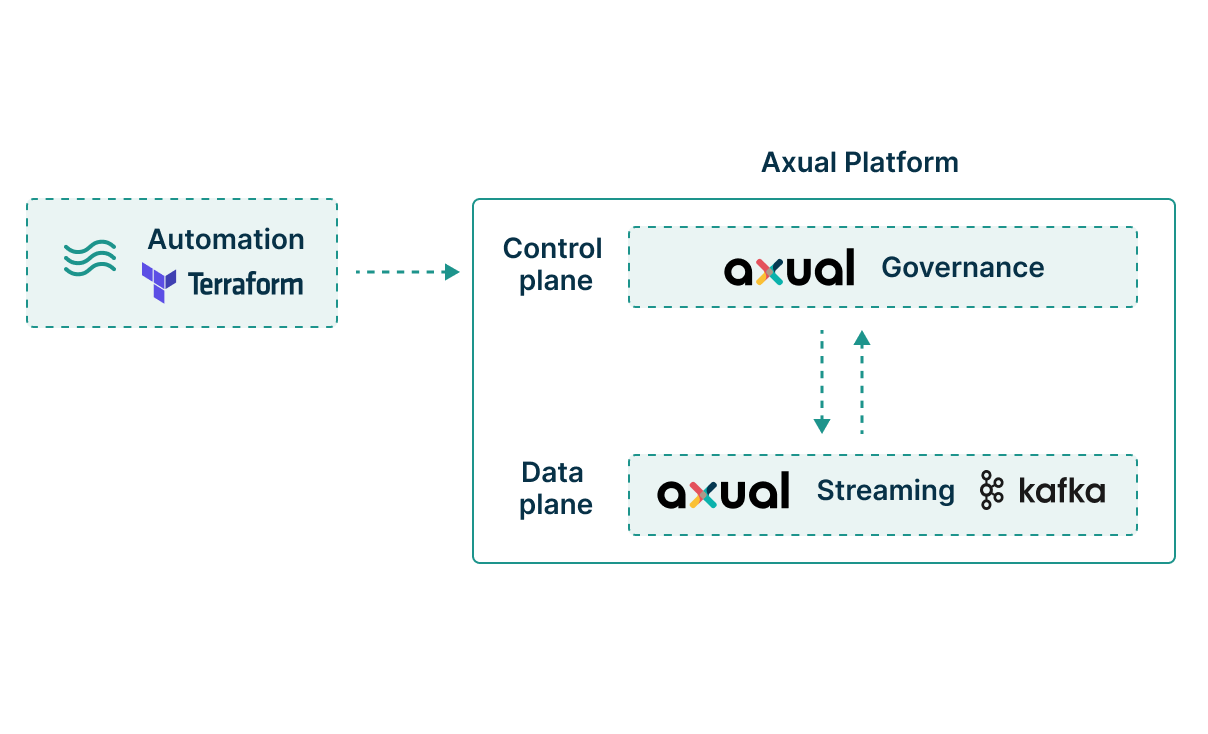
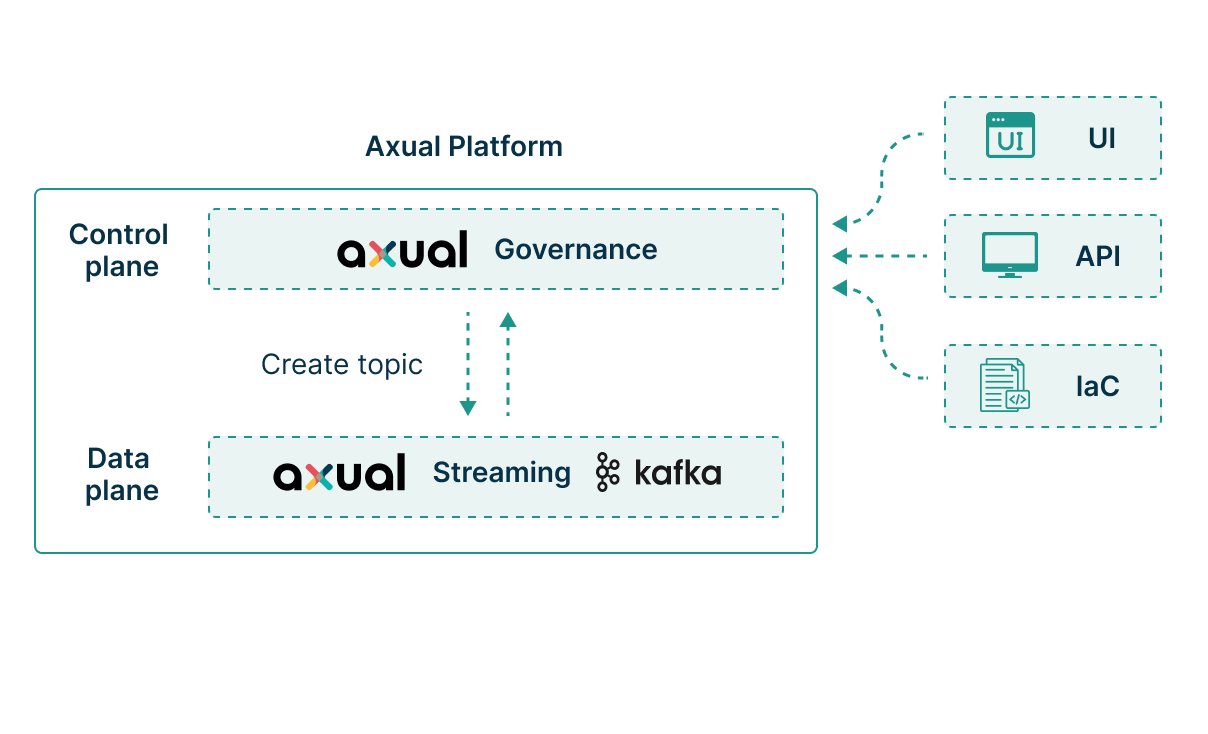
Axual's control plane operates as a separate architectural layer from your Kafka infrastructure, whether that's Confluent Cloud, Amazon MSK, or self managed clusters. This separation means governance operations (creating topics, managing access, updating schemas) never impact message flow. Your producers and consumers continue processing while you address compliance gaps or update configurations. It's a pragmatic design choice: mission critical streams shouldn't fail because someone's updating access controls.
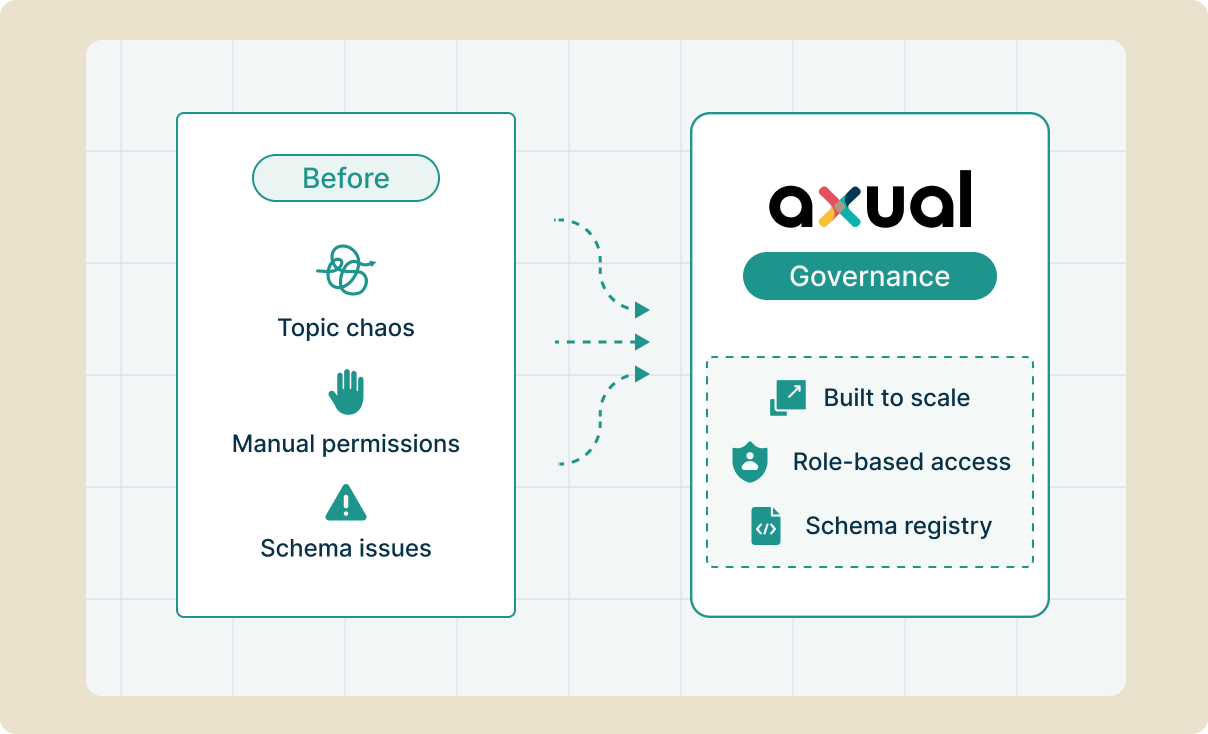
Your current topic naming conventions, ACLs, and operational procedures remain intact. Axual's governance layer wraps around existing deployments without requiring migration or disruption. You gain centralized control across all clusters through a single pane of glass, spanning both managed services and self hosted infrastructure. Think of it as retrofitting governance onto infrastructure that probably grew organically. The platform respects your investments while closing the governance gaps that emerge at scale.
RBAC in Axual maps to your organizational structure through groups and roles. Start with basic roles (Topic Owner, Application Developer) for your pilot team of ten. As you scale to hundreds of users across departments, the same permission model extends through group inheritance and delegated administration. Financial services implementations use this to separate trading system access from risk management data. Healthcare deployments isolate clinical departments while maintaining central oversight. The model that works for your proof of concept remains manageable at enterprise scale.
Absolutely. The Axual Terraform provider treats governance as code. Topics, schemas, applications, and access controls become declarative resources. Your existing CI/CD pipelines deploy Kafka configurations just like application infrastructure. Version control tracks every change, pull requests enforce review processes, and rollbacks restore previous states. This isn't just API automation; it's true infrastructure as code for streaming governance. Your platform engineers manage Kafka the same way they manage Kubernetes.
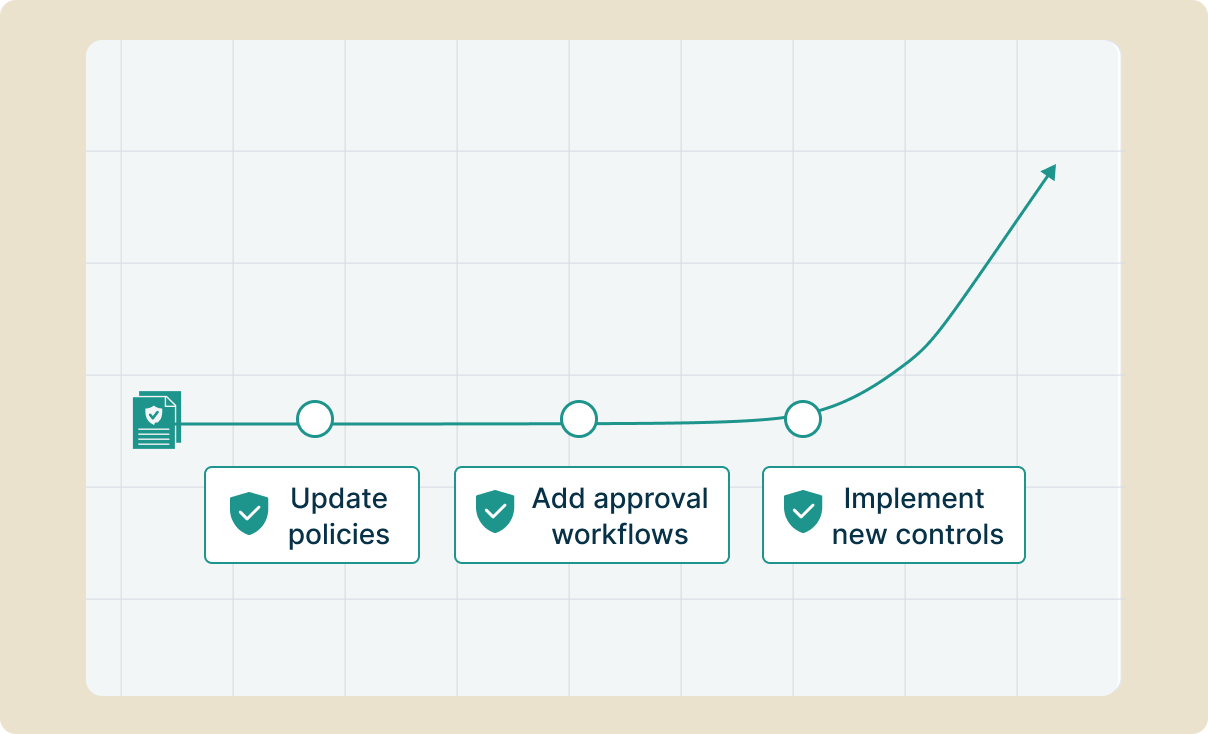
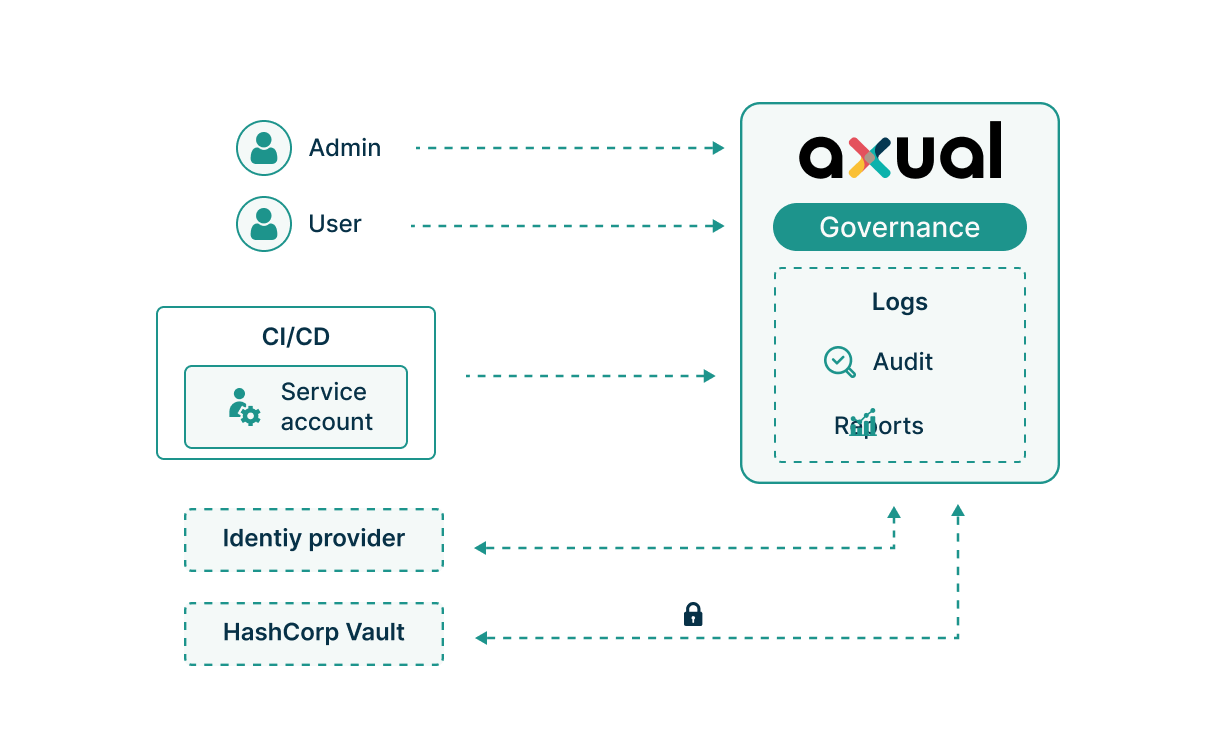
Every governance action creates an immutable audit trail documenting who accessed what, when, and why. Schema versioning tracks data structure evolution for lineage requirements. Role based access satisfies segregation of duties. But here's the critical part: when regulations change (and they will), you update policies through configuration, not architecture. New approval workflows, additional audit fields, or stricter access controls deploy without touching your streaming infrastructure. Your compliance posture evolves as quickly as regulatory requirements.
Less than managing governance manually across multiple Kafka clusters. The control plane runs on Kubernetes with horizontal scaling and automated failover. During governance maintenance, your Kafka clusters continue operating normally. Producers produce, consumers consume. The Platform Manager, API Gateway, and UI are stateless services backed by a single management database. Think of it as trading the complexity of distributed governance for the simplicity of centralized control. Most enterprises find the operational burden decreases compared to their current multi cluster management.
Axual enforces schema compatibility rules before changes reach Kafka. When a developer updates an Avro schema, the registry validates compatibility based on your configured rules: backward, forward, or full. Incompatible changes fail at registration, not when a critical consumer breaks at 3 AM. Every schema version is tracked with full lineage, so you can trace which applications use which versions. This is proactive protection against the schema evolution issues that plague DIY implementations.
Axual integrates with your corporate identity system through OIDC or SAML, whether that's Active Directory, Azure AD, or any enterprise IdP. Users authenticate with their existing credentials, inherit group memberships, and operate within familiar security boundaries. For automation, service accounts use JWT tokens that integrate with your CI/CD security policies. Sensitive credentials (database passwords for connectors, client certificates) store in HashiCorp Vault, never in configuration files.
.svg)
.svg)
.svg)
.svg)
.svg)